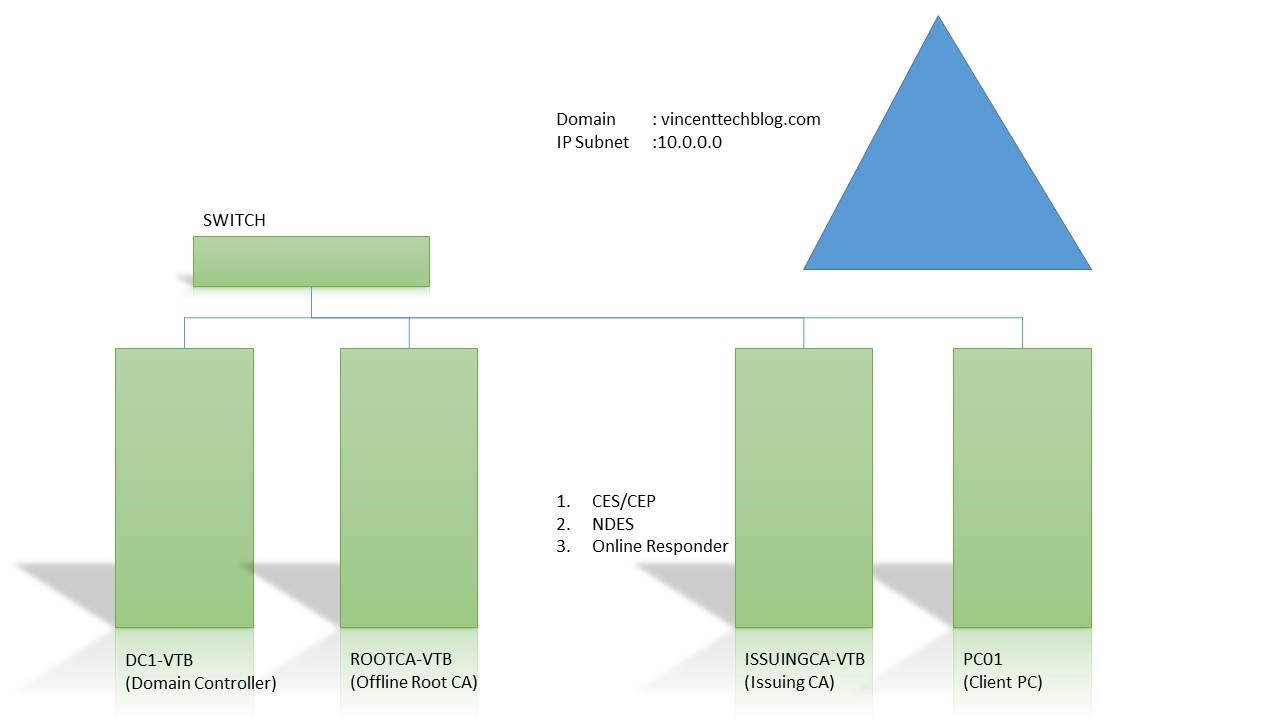
Continuing from our previous configuration, here we will look at;
Certificate Enrollment Service (CES) and Certificate Enrollment Policy (CEP), which where introduced with the Windows 2008 R2 to help a non-domain computer on the Internet connect to the network and be able to enroll for certificates from a Microsoft Enterprise Certification Authority.
Network Device Enrollment Service (NDES) allows software on routers and other network devices running without domain credentials to obtain certificates based on the Simple Certificate Enrollment Protocol (SCEP).
Online Responders are trusted servers that receives and responds to individual client requests for information about the status of a certificate. It is used for conveying information about the validity of certificates. Unlike certificate revocation lists (CRLs), which are distributed periodically and contain information about all certificates that have been revoked or suspended, an Online Responder receives and responds only to individual requests from clients for information about the status of a certificate. The amount of data retrieved per request remains constant no matter how many revoked certificates there might be.
The tutorial shows how to configure all these roles services on the ISSUINGCA-VTB Server which is our Issuing subordinate CA from our last Step by Step tutorial
Content
- Installing Roles
- Configuring Roles
- Setting Up CES and CEP
- Configuring CA Security
- Configuring Certificate Templates
- Configuring Online Responders
or Watch Video
Installing Roles
Step 1 – Switch to the ISSUINGCA-VTB, open Server Manager, Click Manage, and select Add Roles and Features Wizard, Click Next, choose Role-based or feature-based Installation and click Next
Step 2 – On the select Destination server screen, choose your ISSUING-VTB Server and click Next, on the Select Server roles screen, Expand Active Directory Certificate Services role and select as follows
- Certificate Enrollment Policy Web Service
- Certificate Enrollment Web Service
- Network Device Enrollment Service
- Online Responders
On the Additional Features pop-up, click Add Features and select Next
Step 3 – On the select feature screen, leave default and click Next, on the confirm Installation selection screen, thick ‘restart the destination server automatically if required’ and click Install.
Configuring Roles
Step 1 – On the Installation succeeded screen, click ‘Configure Active Directory Certificate’ services on the destination server, on the Credentials screen, ensure you specify the domain admin crediciatials (Mine is VINCENTTECHBLOG\administrator) and click Next
Step 2 – Select all roles to configure;
- Online Responders
- Network Device Enrollment Service
- Certificate Enrollment Web Service
- Certificate Enrollment Policy Web Service
And click Next
Step 3 – Go to DC1-VTB to create a service account which will be used for configurations, Open the Server Manager, Select Tools and choose Active Directory Users and Computers console. Right-Click Users container select New -> User
Step 4 – on the New Object – User screen, enter Svr Agent as First and Last name respectively, and provide Agent as the username, click Next, give a password e.g. pa$$word01, thick User must not change password at next logon, click Next and finish.
Step 5 – Open the user account, switch to the Member Of tab, add the IIS_USERS and the Domain Admins Group and click Ok
After creating the account go back to the ISSUINGCA-VTB and login with the Agent Account (VINCENTTECHBLOG\Agent)
Step 6 – Go to the Administrative Tools, and select Computer Management and further select the Local Users and Groups node, choose Users, open the IIS_IUSERS group, click Add and type ‘Agent’, click Check Names. Your user account shows up, click apply and Ok
Step 7 – On the Service Account for NDES screen, click Select, on the Windows security screen provide the Agent credentials (VINCENTTECHBLOG\Agent) and click Ok, and click Next
Step 8 – On the Registration Authority (RA) Information screen, specify the RA Name, (Mine is ISSUINGCA-VTB-MSCEP-RA) and click Next.
Configuring the Cryptographic service providers (CSPs) and key lengths for signature and encryption keys
Step 9 – On the Cryptography for NDES, leave default and click Next, on the CA for CES screen, leave default and click Next, on the Authentication Type for CES screen, choose Username and Password and click Next, on the Service Account for CES screen, specify the Agent account and click next
Step 10 – on the Authentication Type for CEP screen, select Username and password, on the Enable Key-based Renewal for CEP screen, tick Enable Key-based renewal and click Next
Step 11 – On the Server Certificate screen, Select the Issuing CA certificate and click Next, on the confirmation screen, click Configure
Setting Up CES and CEP
Step 1 – On the Server Manager, from the Tools drop-down, Select Internet Information Services (IIS) Manager, on this console, Select ISSUINGCA-VTB, on the middle pane, double-click on the Server Certificates, then on the Action pane, Click Create Domain Certificate, give a common name of issuingca-vtb.vincenttechblog.com/, other fields are optional, so type the word ‘data’ in all, and click Next
Step 2 – On the Online Certification Authority screen, Specify the Online Certificate Authority certificate (Mine is called ISSUINGCA-VTB.vincenttechblog.com/), give Friendly name of VTB Certificate Authority and click Next.
Step 3 – Select Default Web Site note, on the Actions pane, click ‘Bindings’ and select https and click Edit, on the SSL certificate section, choose VTB Certificate Authority and click Ok and close the Bindings pop-up
Step 4 – Select KeyBasedRenewal_ADPolicyProvider_CEP_UsernamePassword, on the middle/content pane, Select Application Settings, on this screen, double-click Friendly Name and enter ‘VTB Certificate Authority CEP and click Ok.
Step 5 – Right-Click on the KeyBasedRenewal_ADPolicyProvider_CEP_UsernamePassword node and click Switch to Content View, then right-click on the services.svc and click browse
It will open with the browser, edit it as follow and copy it.
https://issuingca-vtb.vincenttechblog.com/KeyBasedRenewal_ADPolicyProvider_CEP_UsernamePassword/services.svc/CEP
Edit the computer and domain name with yours
NOTE – On the Non-domain client, ensure you copy the rootca_Certificate certificate which Is found in the C:\Certs folder and add it to the trusted Root CAs on the non-domain computer.
Step 6 – On the Client computer, goto mmc, on the console, click file menu, select Add or Remove Snap-in, Select Certificate and choose Computer Account and click Ok
Step 7 – Expand the Certificate (Local Computer) -> Trusted Root Certification Authorities -> Certificates, right-click Certificates and select All Tasks->Import.
Step 8 – On the Certificate Import Wizard, click Next and browse for the rootca_Certificate certificate, now you right-click on the Personal Node – All Tasks – Advance Operations – Manage Enrollment Policies, on the pop-up, click Add
Step 9 – On the Certificate Enrollment Policy Server pop-up, in the Enter enrollment policy server URI, enter
https://issuingca-vtb.vincenttechblog.com/KeyBasedRenewal_ADPolicyProvider_CEP_UsernamePassword/services.svc/CEP
Step 10 – in the Authentication type, select username/password and click Validate Server, on the Windows Security pop-up specify the Agent Account credentials (VINCENTTECHBLOG\Agent) and click Ok
Your server should be successfully validated. On the Certificate Enrollment Policy Server console, click add. Now the URI is added
Step 11 – Switch to the Personal node, right-click, select All Tasks, and select Request New Certificate, on the Certificate Enrollment pop-up, click Next, on the Select Certificate Enrollment Policy screen, you will find the CEP we configured and can be used to get a certificate from our Issuing CA.
Configuring CA Security
Step 1 – Go to Certificate Authority console on the Issuing CA, right-click on the ISSUINGCA-VTB node and select Properties, switch to the Security tab and add the user accounts and specify their respective permissions
Step 2 – Switch to the Certificate Managers tab, you can Restrict Certificate Managers based kinds of Templates to be issued and permissions on each templates
Configuring Certificate Templates
Step 1 – Go to Certificate Authority console on the Issuing CA, expand the ISSUINGCA-VTB node and right-click Certificate Templates, and click Manage, on the Certificate Template pop-up, right-click your preferred certificate, e.g. Web Server certificate, right-click on the certificate and select Duplicate Template
Step 2 – On the Properties of new Template pop–up, Switch to the General tab, edit the name and validity period (I gave mine name of VTB Web Server and 2 years’ validity period), switch to the Security tab and select the Authenticated Users group read, enroll and autoenroll, and click Ok to create the certificate
Step 3 – Close the Certificate Template console, on the Certificate Authority Console, right-click Certificate Templates and select New -> Certificate Templates to Issue, on the Enable Certificate Template pop-up, select the certificate template you created, mine is VTB Web Server and click Ok
Step 4 – Switch to the Web Server in your domain and open the mmc console, add the Certificates (Local computer) snap-in from the Files -> Add or Remove Snap-in console, expand the Certificates (Local computer) node, and right-click the personal, select All Task -> Request New Certificate, on the Certificate Enrollment Wizard, click Next, on the select certificate enrollment policy, click Next, on the Request certificates, select the VTB Web Server certificate
Note: if you get and attention message saying more information is required for enrolling for this certificate, click the link to configure settings
Step 5 – On the Certificate Properties pop-up, move to the alternative name section, change the Type to DNS, and type the FQDN (Fully Qualified Domain Name) of the Web server ws-vtb.vincenttechblog.com/, and click Add, then Apply, the Ok,
Step 6 – Select the certificate and Enroll, the certificate will be given immediately.
Configuring Online Responders
Step 1 – Switch back to the IssuingCA-VTB, Open the Certificate Authority Console, right-click on the Certificate Templates node, and click Manage, on the Certificate templates pop-up, right-click on the OCSP Response Signing and click Duplicate Template, switch to the General tab and change the name, mine is vtb OCSP Response Signing, switch to the Security tab and select the Authenticated Users group read, enroll and autoenroll, and click Ok to create the certificate
Step 2 – Close the Certificate Template console, on the Certificate Authority Console, right-click Certificate Templates and select New -> Certificate Templates to Issue, on the Enable Certificate Template pop-up, select the certificate template you created, mine is vtb OCSP Response signing and click Ok
Step 3 – go to Server Manager -> Tools, from the drop-down, select Online Responder Management,
Right-Click on the Revocation Configuration and select Add Revocation configuration, on the pop-uip wizard click Next, on the Name the Revocation Configuration screen, type vtbOnlineResponder, and click Next, on the Select CA Certificate Location, choose Select a certificate for an Existing enterprise CA and click Next, on the choose CA certificate screen, choose Browse CA certificates published in Active Directory , on the Select Certificate Authority pop-up,, choose the Issuing CA Certificate and click Ok and click Next
Step 4 – Your OCSP certificate will be automatically selected, click Next and Finish
We have successfully created our Online Responder
Watch Video